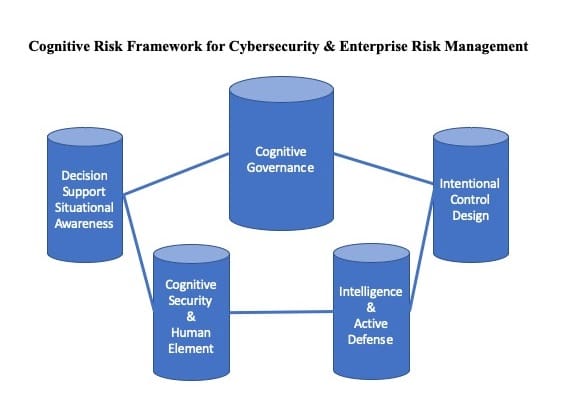
The five pillars of the cognitive risk framework (CRF) are designed to provide a 3D view of enterprise risks. James Bone details here additional levers of risk governance in the final three pillars of the CRF.
In earlier installments, James discussed the first pillar of the Cognitive Risk Framework (CRF), cognitive governance; the five principles undergirding cognitive governance; and the second pillar, intentional control design.
Intentional design, the second pillar, represents a range of solutions designed to manage risks writ large and small. It begins with a clear set of strategic objectives; leverages empirical, risk-based data; then clarifies optimal outcomes. Simplicity in design is the guiding principle in intentional design. Intentional design leverages cognitive governance’s five principles by applying risk-based data to understand how poor workplace design contributes to inefficiencies and hinders employee performance. And intentional design makes the case for design as a risk lever to create situational awareness and incorporates resilient operational excellence into risk management practice. It is an outcome of the analysis in cognitive governance.
Conversely, the third pillar, intelligence and active defense, is a focus on proactive risk enabled by the first two pillars. The first pillar, cognitive governance, is the driver of solution templates for sustainable outcomes using a multidisciplinary approach to address. The next three pillars are additional levers of risk governance.
Introduction
In the early stage of adopting enterprise risk management approaches to information security, Chief Information Security Officers (CISOs) have long recognized the importance of data. However, data alone is not intelligence against an adversary who understands that user behavior is the critical path to achieving its objectives.
CISOs wear multiple hats when multitasking may not be the right approach. One of the many challenges in cyber risk is understanding how to wade through voluminous data to defend against adversaries who operate in stealth mode with weapons that evolve at digital speed. CISOs need help, not a new job title.
Advanced technology provides security professionals with the analytical firepower to analyze data across a variety of threat vectors. CISOs understand that technology only creates scale toward achieving a robust toolset to address the full spectrum of evolving threats. Unfortunately, with billions spent on cybersecurity, a commensurate increase in cyber theft continues to outpace security defenses – the cyber paradox continues!
Intentional design, the second pillar, is a lever to facilitate the third pillar, intelligence and active defense strategies. Designing the right solution set for cybersecurity must also address impacts on IT, organizational and leadership resources. The prime target of attack is the human asset as the weakest link in security. CISOs need help separating the myth of assurance from the reality that exists in their network. Internal and external intelligence about the true nature and changing behavior of threat actors is critical for gaining real insights.
A core use case in cybersecurity targets the insider threat while the biggest cause of data breach is human error. IT security needs empirical data that it can rely on instead of conventional wisdom.
The elephant in the room continues to be a lack of credible data.
IT professionals need a variety of analytical methods to better understand what is actually possible with technology and how to support and enable human assets to recognize and address threats more efficiently.
Threat actors understand the dilemma CISOs face, and they have learned to exploit it to their advantage. This is why CISOs and Chief Risk Officers must collaborate to design not only cyber solutions that deal with poor work processes, but also design continuous intelligence to monitor evolving threats without piling on inefficient security processes. Active defense has been developed as a proactive security response to threat actors. Advanced approaches will emerge out of what is learned by using similar and even more effective tactics.
CISOs have slowly adopted active defense, yet these proactive approaches are becoming more common. Active defense is not hacking the hackers, but the process of designing traps, like honey pots, allowing IT professionals to gain intelligence on threat actor’s and mitigate damage in the event of a breach.
Cyber risk is one of the most complicated risks our nation faces due to the asymmetric nature of the actors involved. Cyber risk is a profitable enterprise in the Dark Web, with everyone contractors-for-hire to designers of advanced threats at the top of the food chain. The market for the most effective tools to achieve criminal objectives ensures that each version is enhanced to gain market share. One-dimensional approaches will continue to leave organizations vulnerable to these threats. An open internet and reverse engineering of customer-facing tech ensures the cyber arms race will only accelerate in the Dark Web. Forward-looking security officers seek solutions that address the complexity of the problem with more comprehensive approaches.
Extensive work done by security researchers has demonstrated that many of the attacks are the result of simple vulnerabilities that have been exploited by attacking human behavior. Simple attacks do not imply a lack of sophistication; hackers use deception in an attempt to cover their tracks and obscure attribution. As organizations push forward with new digital business models, a more thoughtful approach is needed to understand security at the intersection of technology and humans in a networked environment with no boundaries.
 Pillar 3: Intelligence and Active Defense
Pillar 3: Intelligence and Active Defense
This summer I attended a cybersecurity conference and sat in on a demonstration of social engineering. The demonstration included a soundproof booth with a hacker calling a variety of organizations using different personas. The “targets” included every level of the organization; the task was completing a checklist of items that would be used to initiate an attack.
The audience was enthralled at the ease which many of the “targets” agreed to unwittingly assist contestants in the demonstration. Collectively, these approaches are called cognitive hacks, where the target of the hack relies on changing users’ perceptions and behaviors to achieve its objectives.
The demonstration showed how hackers conduct human reconnaissance before an attack is launched. In some of the demonstrations, the “target” was asked to click on links; many complied, enabling the hacker to gain valuable information about the training, defensive strategies and other information tailored to enable an attack on the firm. Prior to the event, contestants developed a dossier on the firms through publicly available information. A few of the “hackers” were not completely successful, but in less than one hour, several contestants showed the audience the simplicity of the approach and the inherent vulnerability of defenses in real time. This is one of many techniques used to get around the myriad cyber defenses at sophisticated organizations.
Deception in the internet is the most effective attack vector, and the target is primarily the human actor.
Pillar three, intelligence and active defense, focuses on the “soft periphery” of human factors. These factors center on the human interaction with technology. As demonstrated above, technology is not needed beyond a phone call. No organization is immune to a data breach when cybersecurity is focused on either detection or prevention using technology.
Defensive and detection strategies, or a combination of approaches, must include the human element. A fourth approach is available that includes a focus on hardening human assets across the firm. Attackers need only to be successful once, while defenders must be successful 100 percent of the time; thus, the asymmetry of the risk.
How does an organization harden the soft periphery of human factors beyond training and awareness? The first step is to recognize there is more to learn about how to address human factors. Technology firms have only begun to explore behavioral analytics solutions using narrow models of behavior. Second, the soft periphery of human factors is a risk-based analysis of gaps in security created by human behavior inside and outside the organization.
Business is conducted in a boundaryless environment that includes a digital trail of forensic behavior that can be weaponized by adroit criminal actors. Defining critical behavioral threats require intelligence that is early-stage; therefore, CISOs must consider how behavior creates fragility in security, then use risk-based approaches to mitigate. Each organization will exhibit different behavioral traits that may lead to vulnerabilities and must be better understood.
As organizations rush to adopt digital strategies, the links between customer and business partner data may unwittingly create fragility in security at the enterprise. Organizations with robust internal security may be surprised to learn how fragile their security profile is when viewed across relationships.
IT professionals need intelligence to assess their robust, yet fragile security posture. Internet of things (IoT), cloud platforms and third-party providers create fragility in security defenses that leave organizations exposed. Organizational culture is also a driver of these behavioral threats, including decision-making under uncertainty.
“A great civilization is not conquered from without until it has destroyed itself from within.”
— Ariel Durant
The third pillar proposes the following proactive approaches as additional levers:
- Active defense
- Cyber and human intelligence analysis
- IT security/compliance automation
- Enhanced cyber hygiene – internal and external human actors
- Cultural behavioral assessment and decision analysis
To save time to cover the remaining pillars, I will not explore these five levers at length; however, I have provided examples in supporting reference for readers to explore on their own. My goal here is to suggest an approach that takes into account the human element in a more comprehensive way. As each pillar is implemented, a three-dimensional picture of risk becomes clear. Intelligence is a design element that adds clarity to the picture.
By way of example, the organizations that fared better than others during the live hack-athon were the ones whose employees practiced strong skepticism and insisted that the caller validate their information with emails, a callback number and a name of a supervisor in the firm. These requests stopped the contestants during the hacker demonstration when the “targets” were persistent in their requests for validating information.
Pillar four is the next lever that deepens insight into enhanced risk governance.
Pillar 4: Cognitive Security and the Human Element
The future of risk governance and decision support will increasingly include the implementation of intelligent informatics. Intelligent informatics is an emerging multidisciplinary approach with real-world solutions in medicine, science, government agencies, technology and industry. These smart systems are being designed to combine computation, cognition and communications to derive new insights to solve complex problems.
We are in the early stage of development of these systems, which include the following burgeoning fields of research:
- machine learning and soft computing;
- data mining and big-data analytics;
- computer vision and pattern recognition; and
- automated reasoning.
The truth is, many of the functions in risk management, compliance, audit and IT security can and will be automated, providing organizations real-time monitoring and analysis 24/7/365, but humans will be needed to decide how to respond.
Advances in automation will both provide new strategic insights not possible by manual processes and also free risk professionals to explore areas of the business that have been inaccessible before. This is not science fiction! Real-life examples exist today, including nurses using clinical decision support systems (CDSS) to improve patient outcomes. An innovation in risk management will be the advent of decision support systems across a range of solutions. These new technologies will allow risk professionals to design solutions that drive decision-making deep into the organization and provide senior management with actionable information about the health of the organization in near real-time.
Risk management technology has rapidly evolved over the last 20 years, from compliance-based applications to integrated modules that automate oversight. GRC applications today will pale in comparison to intelligent informatics that will apply internal and external data pushed to decision-makers at every level of the organization. We are at a crossroads: Organizations are operating with one foot in the 19th century and the other foot racing toward new technology without a roadmap.
Technology solutions that do not improve decision-making at each level of the organization may hinder future growth by adding complexity. A strategic imperative for decision support will be driven by factors associated with cost, competition, product and increased regulatory mandates that challenge organizational resilience. Intelligent informatics will be one of many solutions enabling the levers of the human element.
The human element is the empowerment of every level of the organization by imparting situational awareness into performance, risks, efficiency and decision-making, combined with the ability to adjust and respond in a timely manner. Risk systems are getting smarter and faster, but the real power will only be realized by how well risk professionals learn to leverage these tools to design the solutions needed to help organizations achieve their strategic objectives.
Decision support and situational awareness is the final pillar of a cognitive risk framework. The end product of a cognitive risk framework is the creation of a robust decision support infrastructure that enables situational awareness. A true ERM framework is dynamic, continuously improving and strategic, adding value through actionable intelligence and the capability to respond to a host of threats.
Pillar 5: Decision Support and Situational Awareness
Organizations too often say “everyone owns risk,” but then fail to provide employees with the right tools to manage risks. Risk professionals will continue to be behind the curve without a comprehensive approach for thinking about how to create an infrastructure around decision support and situational awareness.
The five pillars of a cognitive risk framework are designed to provide a roadmap to become a resilient organization. Resiliency will be defined differently by each organization, but the goals inherent in a cognitive risk framework lead to enhanced risk awareness and performance and provides every level of the organization with the right tools to manage their risks within the parameters defined by cognitive governance.
Nimbleness is often cited as an aspirational attribute of a resilient organization; a nimble organization increasingly resembles a technology platform with operational modules designed to scale as needs change. Nineteenth-century organizations are more rigid by design, which reduces their responsiveness to change in comparison to a virtual economy, in which change only requires a few keystrokes. The retail apocalypse is just one of many examples of the transformations to come. A smooth transition to the fourth industrial revolution may depend largely on a digital transformation of the back office and operations.
This dilemma reminds me of a Buddhist saying: “If you meet the Buddha on the road, kill him,” a saying that suggests we need to be able to destroy our most cherished beliefs. We can grow only if we are able to reassess our belief system. To do this, we need to detach ourselves from our beliefs and examine them; if we are wrong, then we must have the mental strength to admit we are wrong, learn and move on.”
Enterprise risk management has become the Buddha, and it is elusive even for the most sophisticated organizations.
A cognitive risk framework builds on traditional ERM approaches to put the human at the center of ERM with the tools to manage complex risks. Isn’t it time to infuse the human element in risk management?
Each of the five pillars have been presented at a minimal level of detail, but there is a tremendous amount of scientific research supporting each of the approaches to achieve a heightened level of maturity for risk governance. A cognitive risk framework for cybersecurity and ERM is the only risk framework based on Nobel-Prize-winning research from Herbert Simon to Dan Kahneman and Paul Slovic, today’s contemporaries of modern risk thinking.
I have referred to cognitive hacks throughout the installments of a cognitive risk framework. Cognitive hacks – which do not require a computer and are based on an attack with the chief objective of changing the behavior of the target to achieve its goals – were first recognized by researchers at the Center for Cognitive Neuroscience at Dartmouth. Hackers have deployed variations of cognitive hacks, such as phishing, social engineering, deception, deepfakes and other methods since the beginning of the internet. The sophistication and deception of these attacks is growing in sophistication, as demonstrated in the 2016 election and continuing into 2020.
Cognitive hacks are a global threat to growth in the fourth industrial revolution. Wholesale destruction of institutional norms of behavior and discourse on the internet are symptoms of the pervasive nature of these attacks. Criminals have weaponized stealth and trust on the internet through intelligence gained by our behavior on the internet. A hidden market of our digital footprint is traded by legitimate and illegitimate players with little to no oversight. Government and business leaders have been caught flat-footed in this cyberwar; IT and risk professionals on the front line of defense lack the resources and tools to effectively prevent the spread of the threat.
Cognitive hacks prey on our subconscious, our biases and heuristics of decision-making. A cognitive risk framework was designed to bring awareness to this growing threat and create informed decision support and situational awareness to counter these threats.
A complete copy of a cognitive risk framework will soon be developed, including a more detailed version in 2020, and more advanced versions of a cognitive risk framework will be developed by others, including myself. I want to thank Corporate Compliance Insights for allowing me to introduce this executive summary.
CSO: Cyber security culture is a collective effort.
Deloitte: Cultivating a cyber risk-aware culture
Forbes: 5 Ways to Fight Back Against Cybersecurity Attacks: The Power of Active Defense
Tripwire: Active Defense: Proactive Threat Intelligence with Honeypots
Forbes: Russian Hackers Disguised as Iranian Spies Attacked 35 Countries
DARPA: Active Cyber Defense (ACD)
DARPA: Cyber Assured Systems Engineering (CASE)
Norton: Good cyber hygiene habits to help stay safe online
Digital Guardian: Enterprise Cyber Hygiene Best Practices: Tips & Strategies for Your Business
NCBI: Improving Cultural Competence
Canadian Journal of Nursing Informatics: Nursing and Artificial Intelligence
Dartmouth: Center for Cognitive Neuroscience
World Economic Forum: The Fourth Industrial Revolution: what it means, how to respond



 James Bone’s career has spanned 29 years of management, financial services and regulatory compliance risk experience with Frito-Lay, Inc., Abbot Labs, Merrill Lynch, and Fidelity Investments. James founded Global Compliance Associates, LLC and TheGRCBlueBook in 2009 to consult with global professional services firms, private equity investors, and risk and compliance professionals seeking insights in governance, risk and compliance (“GRC”) leading practices and best in class vendors.
James is a frequent speaker at industry conferences and contributing writer for Compliance Week and Corporate Compliance Insights and serves as faculty presenter and independent consultant for several global consulting firms specializing in governance, risk and compliance, IT compliance and the GRC vendor market. James created TheGRCBlueBook.com to provide risk and compliance professionals with transparency into the GRC vendor marketplace by creating a forum for writing reviews on GRC products and sharing success stories on the risk practices that are most effective.James is currently attending Harvard Extension School for a Master of Arts in Management with an emphasis in accounting and finance. James received an honorary PhD in Letters from Drury University in Springfield, Missouri and is a member of the Breech Business School Hall of Fame as well as the Missouri Sports Hall of Fame. Having graduated from the Boston University Graduate School of Education, James received his M.Ed. in Management and Organizational Design in 1997 and a Bachelor of Arts in Business Administration from Drury University in 1980.
James Bone’s career has spanned 29 years of management, financial services and regulatory compliance risk experience with Frito-Lay, Inc., Abbot Labs, Merrill Lynch, and Fidelity Investments. James founded Global Compliance Associates, LLC and TheGRCBlueBook in 2009 to consult with global professional services firms, private equity investors, and risk and compliance professionals seeking insights in governance, risk and compliance (“GRC”) leading practices and best in class vendors.
James is a frequent speaker at industry conferences and contributing writer for Compliance Week and Corporate Compliance Insights and serves as faculty presenter and independent consultant for several global consulting firms specializing in governance, risk and compliance, IT compliance and the GRC vendor market. James created TheGRCBlueBook.com to provide risk and compliance professionals with transparency into the GRC vendor marketplace by creating a forum for writing reviews on GRC products and sharing success stories on the risk practices that are most effective.James is currently attending Harvard Extension School for a Master of Arts in Management with an emphasis in accounting and finance. James received an honorary PhD in Letters from Drury University in Springfield, Missouri and is a member of the Breech Business School Hall of Fame as well as the Missouri Sports Hall of Fame. Having graduated from the Boston University Graduate School of Education, James received his M.Ed. in Management and Organizational Design in 1997 and a Bachelor of Arts in Business Administration from Drury University in 1980. 









