Medical devices have been entering hospitals at light speed, which brings up the question of cybersecurity and how providers can maintain safe treatment. Vidya Murthy explores how regulatory actions have impacted medical device cybersecurity and, in turn, patient safety.
The health care industry is a complex web of payers, providers, medical device manufacturers, third-party vendors and, most importantly, patients. Over the last decade, technology has played a central role in advancing quality of care, creating new delivery mediums and changing access for patients, in large part due to the development of new medical devices. The less discussed shift has been viewing cybersecurity as a HIPAA compliance mitigation instead of a patient safety enabler.
Location of Care Delivery
The average hospital bed has 10 to 15 devices connected to it. The American Hospital Association estimates there are about 900,000 hospital beds in 2019, which means there are at least 9,000,000 devices inside U.S. hospitals.
Shifting care beyond health care delivery organizations (HDOs) has increased the ability to treat remote geographies and populations that otherwise couldn’t access an HDO on an ongoing basis. These changes have been great for patients and providers, enabling ongoing monitoring of patients even when they’re not in the HDO. But it also means that some connected devices operate outside of the secured and monitored HDO network while sending data back to providers within the HDO network. The introduction of these connection points also serves as the introduction of additional threat vectors that need to be managed.
HIPAA Breaches and Patient Safety
Frequently perceived as the regulatory burden for HDOs, device vendors and clinicians, HIPAA has had an indelible impact on our health care system. An average of 35 HIPAA violation complaints are made on a daily basis with estimates that 59 percent of the U.S. population has had its health records breached/exposed. Since the compliance date of April 2003, the challenge of complying with the HIPAA rule has persisted.
Beyond the commonly cited identity theft and financial exploitation as a result of a HIPAA breach, a 0.04 percent increase in mortality rates was observed for patients in facilities with a historic breach, even in scenarios where an HDO restored operations and enhanced security controls after a cyberattack. This is surprisingly equivalent to the 0.04 percent possible increase in positive outcome for patients based on enhanced treatments.
Cybersecurity and Patient Safety
The introduction of connected medical devices not only expands the scope of HIPAA management, but also introduces patient safety considerations. What if a glucose meter is manipulated and the attached insulin pump provides an injection that a patient doesn’t need? What if a critical calculation in radiation therapy is manipulated? Even the television show “Homeland” showed a pacemaker vulnerability exploited in an assassination, but this is not the common scenario HDOs and patients face.
The more probable attack using a medical device focuses on a hacker gaining control of an HDO and distributing ransomware. For example, a hacker may compromise an HDO’s network, inhibiting its ability to update electronic health records and use devices that rely on connectivity for delivering care (such as devices used in radiation oncology and sophisticated surgical robots).
While a possible solution may be to revert to pencil and paper during a ransomware attack and delay any elective procedures, delayed capabilities can also result in a re-routing of patients who have emergent needs. Research shows a 13.3 percent higher mortality rate for patients experiencing a cardiac arrest who received a delay in care of four minutes. When applying this finding to a delay in care due to a network takeover by hackers, one can imagine an increase in mortality rates far greater than 13.3 percent.
Regulatory Requirements – Today and Looking Forward
We have heard the FDA rejects drugs, but what may be less obvious is that the FDA has regulatory oversight of the cybersecurity requirements for medical devices.
Issuing their first guidance document in January 2005, the FDA has actively worked to build a collaborative community – including clinicians, hackers, device manufactures and HDOs. Most recently, the PreMarket and PostMarket Management of Cybersecurity in Medical Device documents have created a clear roadmap and goals for the industry to work toward.
While this guidance is noted to still be in draft mode since it was released in October 2018, there are a few areas of focus that it will endorse once finalized (expected sometime in 2020):
- Devices should make extensive use of encryption to keep data private
- Digital signatures should be used to verify authenticity of devices, data and instructions
- Devices should be designed in a way that anticipates regular, routine cybersecurity patches
- User authentication needs to be secure and robust
- Devices should be able to alert users when a cybersecurity breach occurs
Released in 2016, this guidance includes a combination of process and procedural requirements for both medical device manufacturers (MDMs) and HDOs – mainly the following:
- Understanding, assessing and monitoring vulnerabilities and risks
- Robust software life cycle processes that including having a process for ongoing updates and patches
- Threat modeling cybersecurity risks around a medical device
- Participating in a coordinated vulnerability disclosure policy
The FDA has made it clear that MDMs and HDOs must collaborate to successfully build a robust security program. A sample device design process has been diagrammed to better understand the requirements:
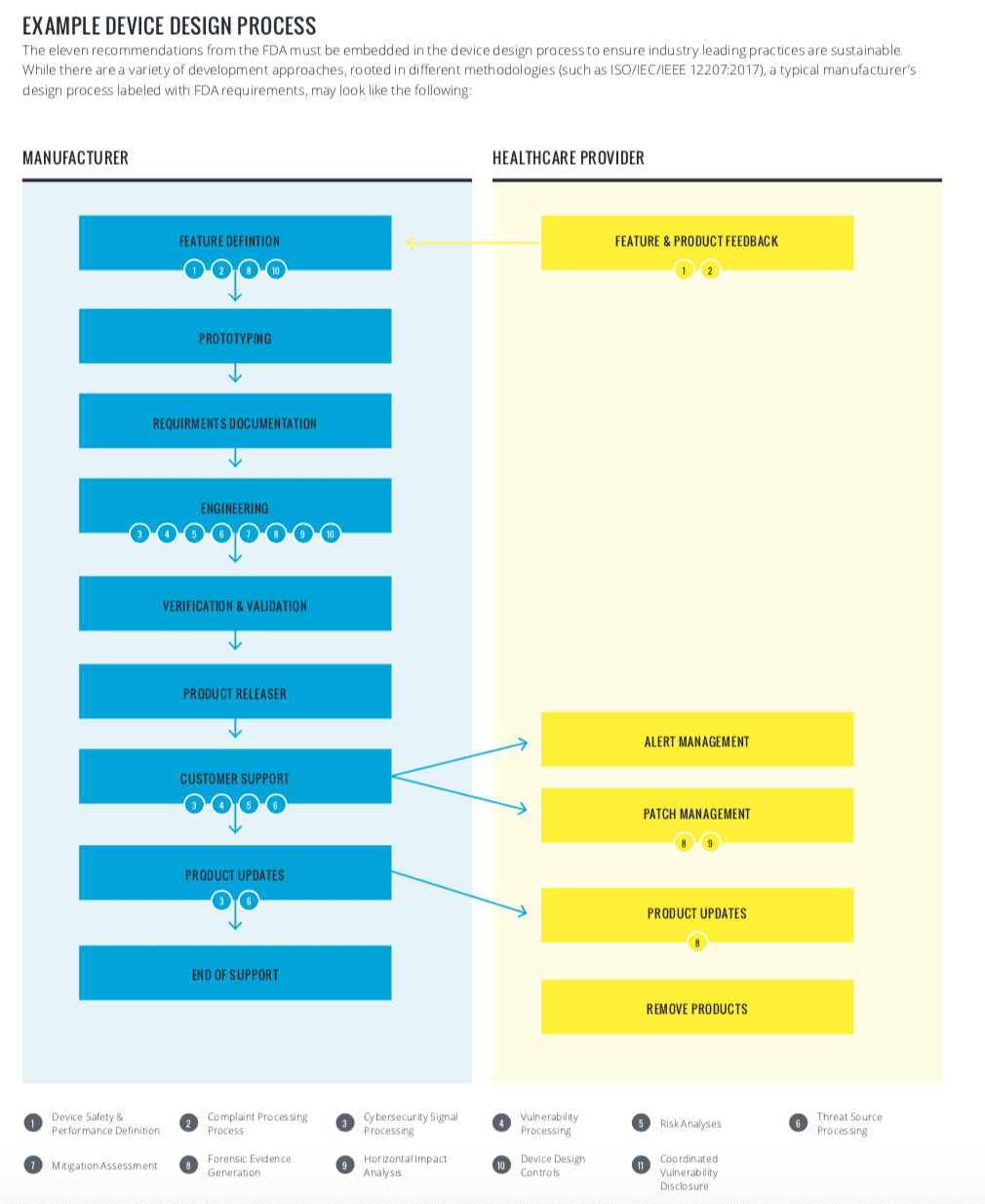
Going Forward
As a compliance practitioner, you are likely skeptical of complicated requirements that are met with the response of “we did it ourselves.” Medical device cybersecurity requires technical and procedural actions by multiple parts of the ecosystem. Leveraging tools as part of an overall security strategy will create scalable and sustainable security.
For products under development, the importance of medical devices being designed with cybersecurity requirements is self-evident. Without these requirements being demonstrated, devices will not receive regulatory blessing.
Those devices that are on the market and still supported by device vendors will stand to gain market share by demonstrating a commitment to implementing cybersecurity requirements. Not for the sake of compliance, but for the patient safety implications of having a robust program in place.
Public and private key stakeholders, including HDOs, medical device vendors, federal agencies and health care IT vendors collaborated to create the Joint Security Plan, a product life cycle reference guide to unite the community on best practices.



 Vidya Murthy is Vice President of Operations at
Vidya Murthy is Vice President of Operations at 









