Risk
Risk refers to threats an organization faces -- loss of earnings, loss of reputation, or harm of any kind. These articles explore the challenges of preventing, identifying and mitigating risk.
Risk can come in many forms, including financial issues, legal liabilities, strategic or leadership errors, or accidents and natural disasters. Today, IT- and data-related risks are growing concerns.
The following articles about risk look at the issue from many angles, especially from that of compliance officers and risk managers.
5 More Common Risk Management Failures
There are a host of ways enterprise risk management can fall short. Jim DeLoach explores five of the most common failures, along with various indicators that could signal a coming failure. If you see your organization reflected in this article, consider this your wake-up call.
Ready for Risk: Painting an Accurate Picture for the Board
The Board is increasingly more attuned to IT risk, and CISOs and CIOs are struggling now more than ever to communicate IT risk data so that the Board can understand its impact. IT leaders are desperate for a way to provide the Board with a concise and accurate risk snapshot that incorporates IT risk into the overall risk posture, shows...
5 Common Risk Management Failures
It’s easy to identify in hindsight where risk management failed, and taking a look at past ERM failures can actually provide great insight into what went wrong and why. Jim DeLoach offers insight into some of the lapses in risk management companies experience most frequently – along with indicators you can be on the lookout for to keep your organization...
12 Steps to Make ERM a Team Sport
Enterprise risk management isn’t meant to be a one-man show. Or a one department show, for that matter. It’s necessary to have the Board’s buy-in and investment. If your firm hasn’t come that far yet, here are a number of simple tips that can help improve your ERM, regardless of where your existing processes stand.
Protiviti: Principles for Improving Board Risk Reporting
Global consulting firm Protiviti has published thought leadership on necessary principles for improving risk oversight. A fundamental underpinning of effective Board risk oversight is timely, reliable and insightful risk reporting. This report discusses six principles for delivering the focused risk reporting the Board needs.
Principles for Improving Board Risk Reporting
Global consulting firm Protiviti has published thought leadership on necessary principles for improving risk oversight. A fundamental underpinning of effective Board risk oversight is timely, reliable and insightful risk reporting. This report discusses six principles for delivering the focused risk reporting the Board needs.
Social Media Sites: An Open Door for Financial Fraud
As the use of social media becomes intertwined with daily business activity, a new threat is emerging: hackers are finding new ways of impersonating genuine business contacts, often portraying colleagues via fake profiles in order to gain access to sensitive data that can be used to commit fraud.
Best Practices for Social Media Archiving and Security
Includes the results of in-depth research survey conducted with individuals responsible for enterprise social strategy at mid-sized and large organizations. It examines the increasing use of social media and the associated risks and costs including malware infiltration, increased in data breach. The paper also has details on the variety of regulatory obligations to retain business records generated by or stored in social...
Using an Effective Policy Structure to Establish Risk Accountability
A large part of effective enterprise risk management is ensuring your policies don’t incentivize (unacceptably) risky behavior. A balance must be struck between revenue generation and risk oversight, and setting clear accountabilities for risk is integral to achieving that balance.
Value Versus Valuation
With the growing awareness of cybersecurity issues and the success of cybersecurity companies, it is no surprise that the industry has captured the attention of venture capitalists. However, the factors that contribute to the industry’s success (high demand and lots of capital) are also the factors that are overcrowding the industry. Now more than ever, investors need to examine the...
Understanding Your Risk Profile
There are significant limitations intrinsic to the traditional approach to risk assessment, which is why a more robust assessment is preferable. Certain categories of risk (strategic, operational, finance, and compliance, for instance) have unique characteristics that cannot be adequately accounted for in a basic assessment.
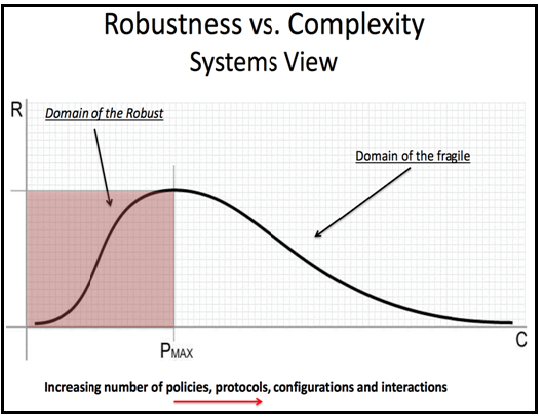
Simplicity Reframed and the Domain of the Fragile
Think of simplicity as an organization's end goal. It's an ideal that can be strived for in product design, process, governance -- you name it. This was the mindset of Steve Jobs as he drove innovation at Apple, and clearly they're doing something right. The benefits of simplicity are far-reaching.