With increased scrutiny from a litany of regulators, cryptocurrency exchanges and financial institutions are now required to monitor, flag and report suspected ransomware payments. Doing so calls for a range of technological capabilities and a sophisticated approach to identifying suspicious patterns in transactions. But compliance teams and the businesses that employ them face stiff consequences if they fail.
As ransomware attacks become increasingly common and threatening, the U.S. government has signaled its determination to prevent them. One of the government’s strategies is to prevent ransoms from being paid to sanctioned actors—and to generate both financial and cyber threat intelligence—through the filing of cyber-related suspicious activity reports (cyber SARs). In particular, the U.S. Department of the Treasury has focused on the role of cryptocurrency or virtual currency exchanges, issuing multiple advisories encouraging exchanges to incorporate ransomware-related risks into their anti-money laundering programs.
Broadly, ransomware is a type of malware that uses encryption to prevent access to a computer system or specific data. Until the ransom is paid, the threat actor holds the system or information hostage, often to devastating operational effect. Ransomware victims span industries as diverse as retail, universities, hospitals, pipelines, food processors and financial services. Threat actors target both public and private institutions. The economic cost has been enormous, rising from $8 billion to $20 billion from 2018 to 2020, and the average ransom demanded has quintupled within the same period. These costs do not even account for the potential safety and security threats presented by ransomware attacks on critical infrastructure or government institutions.
Recognizing the severity of the growing problem, the U.S. Department of Justice (DOJ) announced in June 2021, that it would assign major ransomware cases the same priority as cases involving terrorism. A cornerstone of the policing effort will be to prevent the payment to the threat actors, much of which is currently flowing through crypto exchanges. Among other things, DOJ and FinCEN have proposed stricter regulations and greater transparency requirements for exchanges. The Biden Administration has also recently ordered a review of the regulatory environment of virtual currencies with an eye towards how they are used to fund illicit activities such as ransomware.
Ransomware payments are nearly always made in cryptocurrencies and most of the beneficiary wallets reside at exchanges. Yet, these exchanges accounted for less than 30% of ransomware SARs filed in the first half of 2021. Accordingly, exchanges will need to improve their compliance controls to detect and report potential ransomware payments or face fines or worse. In fact, the very structure of blockchain technology heightens the risk for exchanges, allowing investigators to easily trace suspected payments back to their originators.
Russia Sanctions and Ransomware – A Converging Nexus
On 24 February, Vladimir Putin ordered an invasion of Ukraine. The U.S., E.U. and U.K. responded with devastating sanctions, crippling many Russian industries overnight. However, this has also raised the risk of state-sponsored ransomware. Within days, Conti, a notorious ransomware threat actor, threatened to “strike back at the critical infrastructures [sic]” of Russia’s “enemies.” This raises the risk that prominent ransomware threat actors may be the subjects of future sanctions, or their actions may be tied back directly to other sanctioned actors. In response, FinCEN issued an advisory on Russian sanctions evasion which noted—without naming specific threat actors—the threat of increased ransomware attacks and financial institution’s obligations to adhere to sanctions and file suspicious activity reports in a timely fashion.
Virtual currency exchanges have a small window to take the initiative and design robust ransomware-related compliance controls to protect their own businesses, before U.S. agencies and regulators push out their requirements instead. Exchanges should consider using this time to enhance their compliance controls to identify accounts likely to make or receive ransom payments and ensure that they have policies, procedures, and technology in place to satisfy their sanctions screening and suspicious activity reporting obligations relating to ransomware.
Want to read more about how banks are attempting to track and report ransomware payments? Check out further insights here.
Ransomware Compliance Obligations
Traditional anti-money laundering (AML) and sanctions compliance programs are not well equipped to address the unique challenges posed by the recent FinCEN and OFAC advisories. Specifically, the Treasury Department advisories:
- Prohibit the payment of ransoms to sanctioned persons; and
- Require financial institutions, including cryptocurrency exchanges, to file suspicious activity reports (“SAR”) on ransomware payments which should include “cyber-related information and technical indicators” such as forensic evidence of intrusions on the victim’s network (“indicators of compromise” or “IOC”).
These requirements present multiple challenges. First, ransomware threat actors (especially those operating under a common Ransomware-as-a-Service model) often use money laundering tactics designed to accommodate their specialized infrastructure. Second, threat actors try to mask their identities. The incident response team may not be able to attribute an attack to a certain threat actor or may not know all the relevant information to meet OFAC and FinCEN’s requirements at the time the ransom is paid.
To remain compliant, cryptocurrency exchanges must deploy transaction monitoring scenarios to identify ransom-related payments, as well as provide their compliance departments with specialized skills and technology to investigate the leads generated by those scenarios and work with the payees to address compliance issues. Attributing an attack to a threat actor or reaching a level of comfort with a payment requires detailed analysis of any clues the attacker has left behind. Cryptocurrency exchanges must detect both inbound and outbound ransom payments, collect technical information on the attack, and analyze it.
Accordingly, exchanges must combine transaction monitoring programs with cybersecurity expertise that understands the different threat actors and how to obtain and analyze IOC to properly assess the sanctions risks and provide the necessary SAR information.
Monitoring and Screening Guidance
Exchanges should monitor for both inbound and outbound ransom payments, each of which require separate scenarios and assessment techniques. Darkside’s infamous attack on Colonial Pipeline is illustrative:
- The outbound ransom was paid from a prominent exchange to an intermediary wallet, and the money was transferred to an administration account used by DarkSide (“admin account”) to distribute the ransom payments.
- The admin account collected the ransom and may distribute the shares of the payment to the various actors, who had specialized roles, such as identifying the exploit (i.e., system vulnerability), deploying the malware (i.e., executing the attack), and negotiating the ransom or a RaaS admin account may collect their fee (which will remain in the admin wallet) and then distribute the remainder of the ransom to the actual attacker’s account.
- After the funds are distributed, each party (or owner of each wallet) may begin structuring the funds which would eventually arrive at a cryptocurrency exchange. Threat actors may launder the funds through various methods (described in Section B below). In particular, the threat actor may use exchanges to cash out on the ransom or “chain-hop” by transferring assets from a traceable blockchain to another.
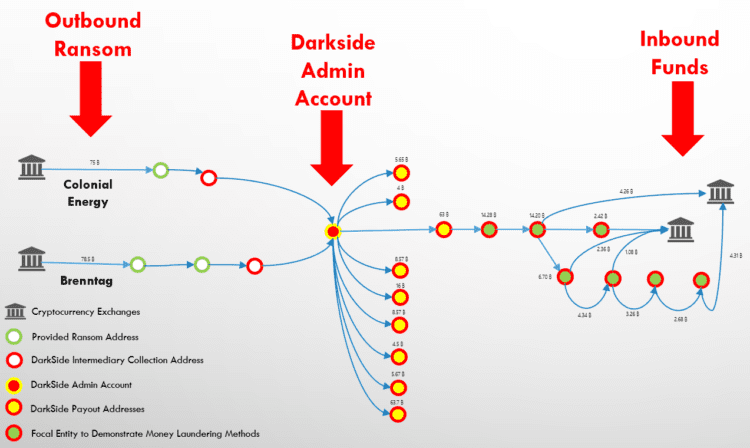
While traditional transaction monitoring systems are necessary to detect those transactions that indicate money laundering, exchanges should also invest in technologies and processes that allow them to explore a particular transaction’s history to identify the financial infrastructure supporting ransomware threat actors (e.g., admin accounts, mixers, etc.). Exchanges will therefore need to implement account-level transaction monitoring capabilities alongside a blockchain explorer, which provides current information on known threat actor accounts.
A. Outbound Ransom Payments
When detecting outbound activity, exchanges should focus their transaction monitoring and KYC programs on identifying victims of ransomware or companies which may facilitate ransom payments. By focusing on KYC and initial account activity, exchanges can detect ransom payments before they are made by:
- Identifying digital forensic and incident response (“DFIR”) firms, insurers, or ransomware payment specialist firms who maintain accounts at the exchange, and who may remit ransom payments on behalf of their customers;
- Identifying customers who state that the purpose of their account is to pay a ransom, or who immediately fund the account with a large sum, or large round amounts (after accounting for exchange fees); and
- Identifying customers who are part of industries which are classified as the 16 critical infrastructure industries by the U.S. Cyber and Infrastructure Security Agency.
DFIR firms, insurers and ransomware payment specialists are likely to make multiple ransom payments through an exchange. If the exchange’s policy is to allow ransom payments, it should engage the account holder and establish a process to stop and scrutinize all payments from the firm. Equally importantly, exchanges should also consider whether the DFIR or payment specialist is remitting money on behalf of their client, whether they have registered as a money service business, and the legal implications of maintaining an account for a person operating as an unlicensed MSB.
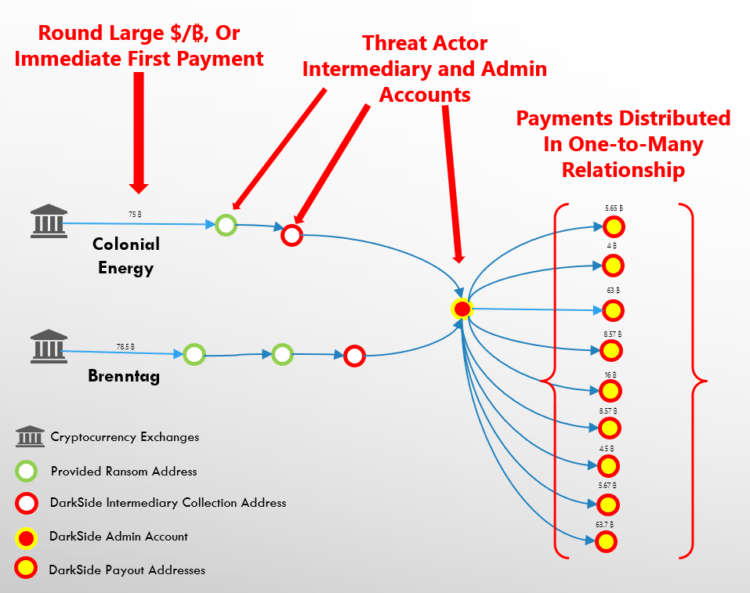
A robust transaction monitoring program should complement the KYC process. Exchanges should use specialized blockchain explorer software and more traditional transaction monitoring scenarios to analyze movement at the account level and to monitor downstream transactions which conform to known typologies. When possible, these scenarios should have their thresholds and parameters set based on rigorous testing. Some considerations include:
- Ransoms are typically paid by victims in a single transaction. The ransom may be a round payment (sometimes allowing for exchange fees) or a large initial payment from a new customer. Victims may accidentally pay a ransom without accounting for an exchange fee and may therefore make a second payment for a lower value quickly thereafter.
- Large value transactions which rapidly move between two or more accounts may signify the use of intermediary accounts. This movement may not occur immediately, and investigators should build in a “follow-up” period to determine where the transaction may have gone.
- Funds that are broken into a one-to-many relationship after being transferred through several intermediary wallets may signify admin accounts.
B. Inbound Ransom Payments
Transaction monitoring scenarios to detect inbound ransom payments should focus on traditional cryptocurrency laundering techniques or money laundering techniques and work backwards to identify the structure of ransomware admin accounts. This may require using more than one tool, such as account-level transaction monitoring systems to identify suspicious activity, and blockchain explorers to analyze provenance. Certain blockchain explorers can also provide real-time alerts which may indicate that a transaction is coming from a suspicious source, including known ransomware-related addresses.
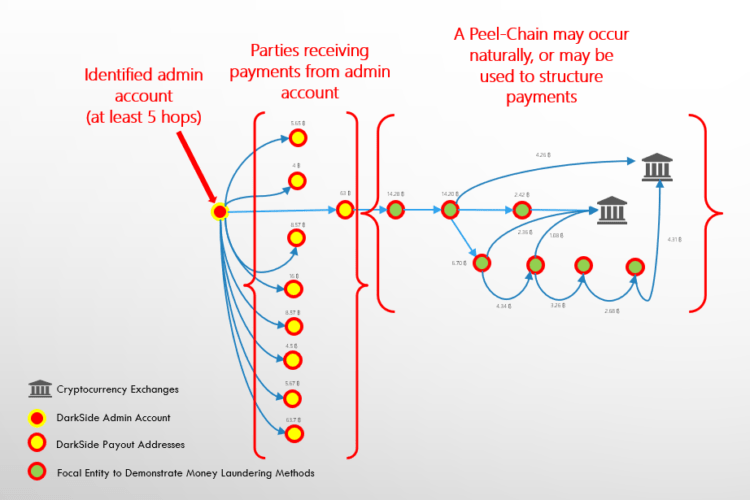
Using transaction monitoring systems, exchanges can identify potentially suspicious accounts using the following scenarios:
- Rapid movement of funds over a certain value threshold, and where the funds are retrieved through multiple rapid ATM withdrawals, or where funds are remitted on to a high-risk exchange;
- Accounts which aggregate funds in a many-to-one relationship; and
- Accounts which receive multiple small transactions and transfer funds: (i) between one cryptocurrency to another in a rapid timeframe, (ii) to a currency which allows them to cash out the account, or (iii) where the customer rapidly cashes out the funds.
Beyond their utility in examining transactions involving an alert, certain blockchain explorer technologies integrate negative news research and can identify high risk transactions in real time. Exchanges should consider reviewing transactions relating to the following alerts:
- Alerts involving uncommon peel-chains should be followed back by at least five hops to determine if they are received from accounts which display the indicia of suspicion listed below.
- Funds received from known ransomware-related admin accounts, which may be previously identified through blockchain explorer platforms.
- Large transfers from mixers, whose service has been increasingly used by ransomware threat actors.
- Outbound transactions to known infrastructure sources which ransomware actors may use, including dark net markets (for the provision of stolen credentials) and certain internet services, which may be used for anonymization (e.g., CDNs), command and control infrastructure, and other known bulletproof hosting services.
C. Managing Alerts
At a minimum, exchanges should establish a policy towards ransom payments and procedures to adjudicate these alerts. If feasible, exchanges should maintain a specialized unit to manage ransomware alerts (“ransomware units”) or train people within the AML program to specifically to handle cases as they arise. The ransomware unit should identify platforms and technologies which can be used to support this effort, including threat intelligence platforms which provide information on threat actors and their IOC.
An exchange has two priorities when adjudicating ransomware-related alerts: (i) determining, based on the information available, whether the threat actor or ransom is prohibited by sanctions, and (ii) gathering enough information to file a complete suspicious activity report. Both objectives require the exchange to gather information on the attack. Exchanges will be better able to collect information on outbound ransoms when the customer must provide information through a request for information, as opposed to inbound payments which may rely more heavily on an analysis of money laundering techniques and upstream payments.
D. Sanctions Screening
OFAC prohibits exchanges from facilitating ransom payments to sanctioned parties, while acknowledging the inherent difficulty in accurately identifying sanctioned threat actors. In essence, OFAC expects that exchanges will engage in a good faith effort to conduct sanctions due diligence on ransom payments.
Accordingly, exchanges should consider a risk-based approach, which, at a minimum, would include measures to ensure that the information available at the time of the ransom payment does not indicate a sanctions nexus. Some measures might include:
- Obtaining an attestation from the account holder that they have conducted sanctions due diligence into the attack, including screening the threat actor, digital currency address, and ensuring that discovered IOC do not indicate a sanctions nexus (e.g., an IP address that leads to a sanctioned country, a malware hash-file previously used by a sanctioned party, etc.);
- Comparing the IOC to information in threat intelligence tools and resolving all IP addresses to determine if the IOC have been previously associated with a sanctioned threat actor;
- Conducting research into the suspected threat actor to determine if a threat intelligence platform or a government agency (e.g., CISA, OFAC, FBI) have associated the threat actor with a sanctioned party; and
- The threat actor review should do its best to adhere to methodologies used by the government to analyze and classify threats (e.g., Mitre ATT&CK – a cybersecurity framework used by the U.S. government).
This process may need to be undertaken iteratively, because the account holder may not have collected all information before a ransom payment. Exchanges should establish procedures to make risk-based decisions on when a payment is permissible and should commit to following through with the collection of all relevant information after the fact. If possible, an exchange should attempt to obtain a copy or the incident response report or an annex with all IOC and tactics later discovered. OFAC places a high priority on U.S. persons who cooperate with law enforcement and meet their own compliance obligations when determining whether to bring an enforcement action.
E. Filing a SAR
Suspicious Activity Reports (“SAR”) play a central role in rooting out threat actors. Thus, regulators will likely increase focus on not just the quantity, but quality of SARs filed by exchanges. A helpful ransomware SAR will include the following information:
- Identification of the parties or suspected parties, including the account holder, likely threat actor, and any third parties involved in the ransom payment;
- Financial information relating to the transaction, including account numbers or digital currency wallets, other exchanges or institutions, and the methodologies used by the threat actor to launder the ransom payment; and
- A list of all IOC the exchange was able to collect during the investigation.
Filing an effective SAR will require the exchange to go through the steps discussed in the section above, but FinCEN expects that exchanges will file a SAR on all suspicious activity (i.e., all ransom payments), not just ones which may be subject to sanctions.
Moving Forward
Ransomware attacks present a growing and imminent danger to the health and safety of individuals and institutions, and the U.S. government is moving swiftly to ensure that the ransom payment process does not benefit sanctioned actors, generates significant financial intelligence, and ultimately undercuts all malicious cyber actors.
The U.S. government and regulators are likely to focus heavily on the ability of cryptocurrency exchanges to comply with both money laundering and sanctions regulations. Unlike traditional wire payments, blockchain payments can be publicly traced back to their source and provide a strong argument for enforcement agencies to focus on less-compliant exchanges. The DOJ’s investigation of Binance may be a preview to a new round of enforcement actions. Strong controls are critical in not only protecting the exchanges from regulatory or criminal penalties, but also in protecting global economic, reputational and security interests.



 Daniel J. Chirlin represents individuals and organizations in criminal, civil and regulatory matters as senior counsel at Walden Macht & Haran, LLP in New York. Dan represents individuals and organizations in criminal, civil and regulatory matters. He also has significant experience leading complicated internal investigations and has defended clients in a wide range of business crimes and investigations-related inquiries. He can be reached at 212-335-2956 or
Daniel J. Chirlin represents individuals and organizations in criminal, civil and regulatory matters as senior counsel at Walden Macht & Haran, LLP in New York. Dan represents individuals and organizations in criminal, civil and regulatory matters. He also has significant experience leading complicated internal investigations and has defended clients in a wide range of business crimes and investigations-related inquiries. He can be reached at 212-335-2956 or  David Tannenbaum founded Blackstone Compliance Services, a company specializing in sanctions compliance after leaving the Office of Foreign Assets Control of the United States Department of the Treasury (OFAC) in 2013. David has led sanctions testing for three major monitorships on behalf of the United States Department of Justice (DOJ), Federal Reserve Board (FRB) and New York Department of Financial Services (DFS). David has provided advice and assistance to financial institutions, high-risk companies and oil field service providers in over 20 countries to help them design their sanctions programs, conduct complex investigations and implement compliance technologies.
David Tannenbaum founded Blackstone Compliance Services, a company specializing in sanctions compliance after leaving the Office of Foreign Assets Control of the United States Department of the Treasury (OFAC) in 2013. David has led sanctions testing for three major monitorships on behalf of the United States Department of Justice (DOJ), Federal Reserve Board (FRB) and New York Department of Financial Services (DFS). David has provided advice and assistance to financial institutions, high-risk companies and oil field service providers in over 20 countries to help them design their sanctions programs, conduct complex investigations and implement compliance technologies.