12 Steps to Reveal and Reduce Cyber-Breach Risk
One hundred percent of businesses are or will be victims of a cybersecurity breach, disruption or attack — either directly or indirectly. No one is immune. That’s why this article is not just for the Fortune 500 CISO or the fortunate few with arms-race-level cybersecurity expertise. It’s for everyone else, too.
Charles Dickens said we live in tumultuous times, and that was in 1859. Back then, they physically chopped off your head in a gruesome spectacle via guillotine.
While the cyber-breach head-chopping that occurs in our own interconnected and tumultuous times is not quite as gory, the results of this financial, reputational and emotional chopping block can be almost as scary. The threat — and the need to protect yourself — is constant.
For example, Facebook recently admitted that around 90,000,000 people have been subject to possible data exposure and privacy loss. That means the events happened months ago, and today’s risk levels are probably worse.
Cyber-breach vulnerabilities and resilience are now on every major organization’s risk agenda — so long as someone else handles it.
Why? Partially because who – other than CISO’s and a few others – really understands terms like cyber breach, COBIT, SIEM and digital forensics?
So, let’s help you get a little more comfortable with the subject and improve corporate governance insights in this era of heightened liability and global asymmetric risk.
Your Cyber-Risk Framework
Create a framework for assessing your business’s cyber exposure by starting with this simple two-minute exercise.
Step 1. Answer the following two questions on a scale of 1 to 10:
Awareness: If 10 means you could lead a cyberthreat panel discussion and 1 means you are not comfortably sure about your real level of cyber-risk preparedness, how aware is your business?
Investment: If 10 means you have conducted in-depth and sophisticated cyber and security overviews and are implementing all those recommendations and 1 means minimal budget is available until next year or later, at what level is your business investing?
Step 2. Mark your answers on the two axes in the Cyber Awareness Versus Investment graphic below.
Mark your numerical answer for Awareness on the horizontal continuum from Leader to Novice and your answer for Investment on the vertical continuum from Reasonable Investment to Minimal Investment.
Draw a line between the two points to note your cyber awareness and indicate where you should begin in the 12-step process that follows.
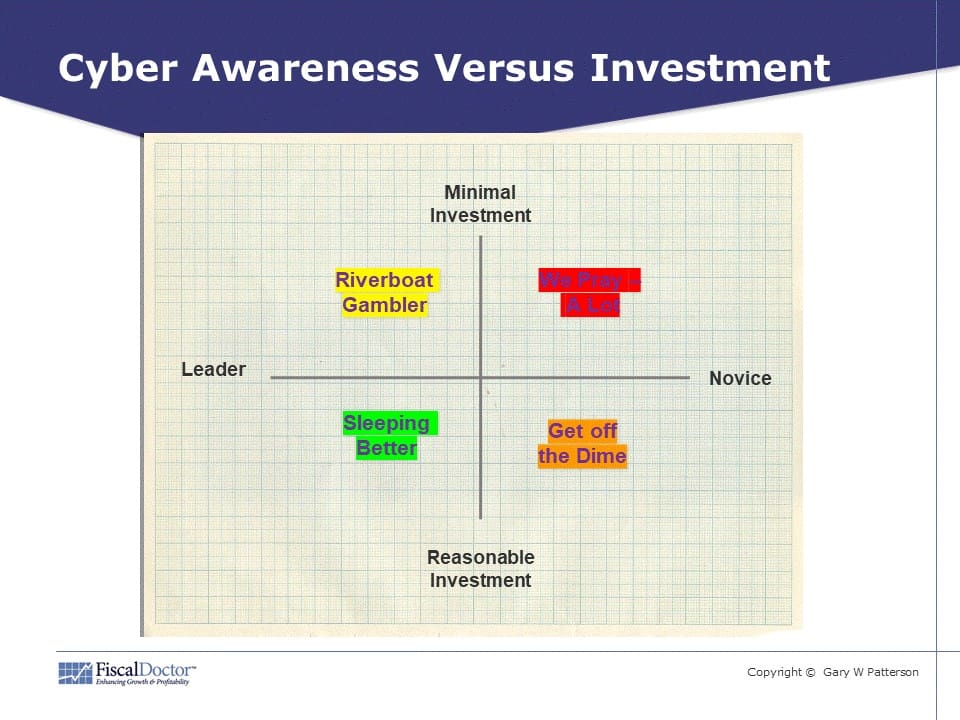
Step 3. Consider the implications of the quadrant your business falls into:
We Pray — A Lot in the upper right suggests limited, even minimal, budget for cyber-risk management and control, combined with limited, even novice, understanding of your cybersecurity risks at the top management and board level.
Riverboat Gambler in the upper left represents those who are aware of both cybersecurity and possible cyber exposures, but prefer to kick most cans down the road, addressing issues slowly and hoping their business won’t be attacked.
Get Off the Dime in the bottom right suggests a reasonable cyber-risk management budget, but only a limited proactive appreciation of specific cybersecurity vulnerabilities that may originate from your supply chain and third-party vendors.
Sleeping Better in the lower left suggests a strong understanding of strategy and operational cyber issues beyond IT, along with executive-level commitment to manage risks (and the accompanying political clout and resources needed).
12 Suggested Best-Practice Steps to Move Forward
This 12-step process was developed thanks to anonymous input from the highly experienced attendees at the 2018 NACD (National Association of Corporate Directors) Global Board Leaders’ Summit. Their insights and suggested actions have been aggregated into 12 transformative steps for improving checks and balances. In a world where far too many people enjoy second-guessing well after the fact, your potential million-dollar blind spots are better found and resolved as part of your enterprise risk management (ERM), compliance or governance processes — united to minimize silos.
Keep in mind that initially, many people do not accurately know what they do not know about cyber risk. Use the 12 steps below to gain the knowledge you need and learn what actions to take.
12 steps to reduce cyber risk, grouped by quadrant, with a maximum of three actions per quadrant
At the end of each quadrant section, compare your overall progress to where you need to be on your cyber journey to move confidently into the next quadrant.
Quadrant I: We Pray – A Lot (limited financial resources, low cyber understanding)
1 – Search and obtain all internal or external reports on cybersecurity, enterprise risk management, crisis management, governance, risk management assessment or business continuity to determine your initial baseline.
2 – Arrange a series of basic, independent external tests, including a penetration test.
3 – Conduct a basic cyber-risk assessment of processes and highest vulnerabilities.
At this point, you should have a somewhat detailed awareness of exposure magnitudes.
Quadrant II: Riverboat Gambler (limited financial resources, reasonable cyber understanding)
4 – Set a board-level cyber-risk tolerance that is supported by top management’s execution plan.
5 – Compare this to client and vendor expectations and near-term and future competitors’ cyber capabilities.
6 – Make sure resources are appropriate to protect the most crucial assets at risk: the “corporate crown jewels.”
At this point, most people have an initial categorization of known issues and are addressing exposures.
Quadrant III: Get Off the Dime (reasonable financial resources, low cyber understanding)
7 – Reallocate and increase funding where needed to align with assessed risks and tolerance.
8 – Execute on the full cyber roadmap to protect corporate and reputational assets.
9 – Ensure cybersecurity is a Top-5 priority for your CEO.
At this point, you should have created your own unique roadmap and at least begun implementation of recommended actions.
Quadrant IV: Sleeping Better (reasonable financial assets, reasonable cyber understanding)
10 – Continually monitor and update to protect your most crucial assets and infrastructure.
11 – Include cyber updates and monitoring in the corporate incentive plan for all top management, not just the CISO, CTO and CFO.
12 – Review and revise all policies, training and oversight on a set and regular schedule.
Congratulations! Your initial plan is set and underway, with postmortem adaptations scheduled and regularly updated. Now, move forward to the more expansive applications needed to keep yourself better prepared against the “Bad Guys” (who never sleep). And remember, security is always about trade-offs.
Call to Action
Using the process above, it is possible to get a reasonably accurate understanding of your business’s major invisible cyber risks. You can strategically evaluate the major cyber holes and blind spots specific to your organization. Then rinse and repeat, as ERM experts counsel.
Cyber breaches cost jobs, destroy reputations and dramatically impact brand value. Add in speed-of-sound lawsuit responses and doing nothing — or the very least possible — becomes a scary option. Standing still after getting the basics underway is also not an option. The hackers are continually escalating the nature, sophistication and magnitude of their attacks.
You probably recognize that good enough last year, as compared to the competition for your sector, size, company, etc., is not good enough this year. At a minimum, consider documenting why you believe that what you have decided on is good enough this year. Remember that the people making judgments — when, not if, you suffer a cyber breach — will use hindsight and an agenda biased against you and your business.
It’s still a tumultuous world out there, but you can take steps to protect yourself from the bad guys. Consider these 12 proven suggestions and apply those that make the most sense at this point in your organization’s life cycle. Taking any of these actions will help reduce your exposure to cyber-breach risk and strengthen the related areas of ERM, compliance and governance.



 Gary W. Patterson, president & CEO of
Gary W. Patterson, president & CEO of 









